Mobile Security testing with SmartQE
Mobile Security testing with SmartQE
SmartQE is a containerized Cloud based SaaS opensource framework for mobile native, hybrid and Web platform code inspections and validate against standards. SmartQE can easily integrate CI/CD platforms and tools.
Mobile Security testing is a process to determine that an information system protects data and maintains functionality as intended. The six basic security concepts are confidentiality, integrity, authentication, availability, authorization and non-repudiation
- Availability: Assuring that information & communications services are available and maintained for authorized persons when needed.
- Authentication: Assuring the validity of any type of originator, transmission or message. This also gives confidence that information is received by a known and validated source.
- Authorization: Assuring that an individual can allow/deny access to a system/service/operation (e.g. Access control).
- Confidentiality: Ensuring information is accessible only for those with authorized access and to prevent information disclosure to any party other than the intended recipients. Often ensured by encoding information using algorithms (cryptography).
- Integrity: Ensuring received information is preserved successfully with no alteration.
- Non-repudiation: Ensuring action/communication cannot later be denied (usually used by form of authentication and time stamping).
Mobile Applications
Mobile web and Apps are becoming a progressively common platform for supporting both business and free time activities
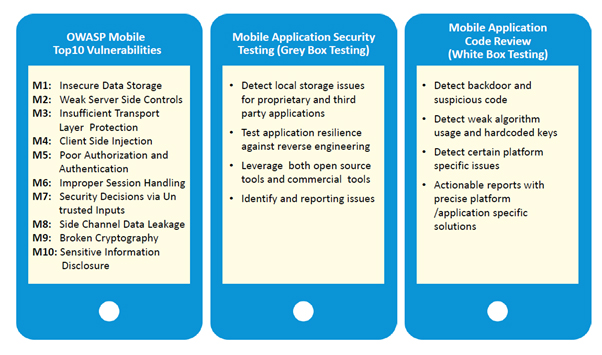
Mobile Security Testing Types/Coverage
- Comprehensive Testing: Flexible application security testing program that includes both static code analysis and regularly scheduled dynamic scans that do not interfere with software innovation & rapid releases, Test vulnerabilities, weaknesses in communications and sensitive data storage
- End-to-End Security: Security assessments of source code, binaries and the running application itself to find vulnerabilities across the three tiers of a mobile application: client, network and server
- Malware Discovery: Mobile standard and premium scans include real-world environment testing to produce behavioural information and thorough malware discovery.
Why do you need mobile application security testing?
- Mobile application can essentially live in the public domain - leaving it open to global scrutiny and the potential for malicious exploitation.
- Insecure mobile applications can introduce attack vectors against the services they offer, the data they process and the users of the application.
- It is inevitable with the growing popularity of mobile applications being used as the preferred interface between a user and network resources that security breaches achieved through such a channel become more widespread.
- Breaches of this nature can damage the reputation and public levels of trust in mobile apps published by organizations and any associated third-party developers.
- The Threat to Cybersecurity is increasing day by day as Organizations are concentrating more on integrating variety of applications overlooking the security risks. Not only the hackers are adopting extremely advanced Techniques but also there are not enough cyber security professionals to tackle them.
- Distributed risks (Data segregation, Leakage of private information, Service loss, Malware attacks)
- Access to sensitive data stored on the device
- Access to data stored on corporate networks
- Malicious software
- Ability to impersonate the authorized user
- Lack of security standards
- Weak Authentication
- poor Authorization
- poor Integration
- Missing Security Configurations
- Explore the internal network
- Directory Traversing
- Injections
- Parameter Manipulation
- Distributed risks (Data segregation, Leakage of private information, Service loss, Malware attacks)
Mobile Security Testing
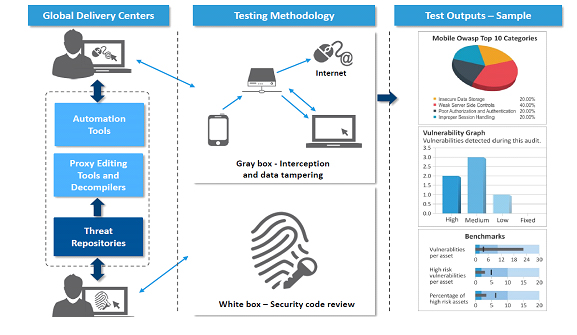
Mobile Security Testing Key Focus Areas
Mobile Threat Assessment
 Network Penetration Testing
Network Penetration Testing
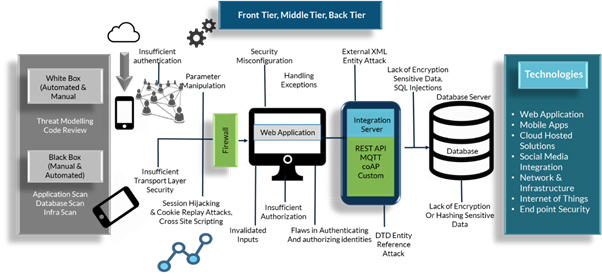
Source Code Analysis Process
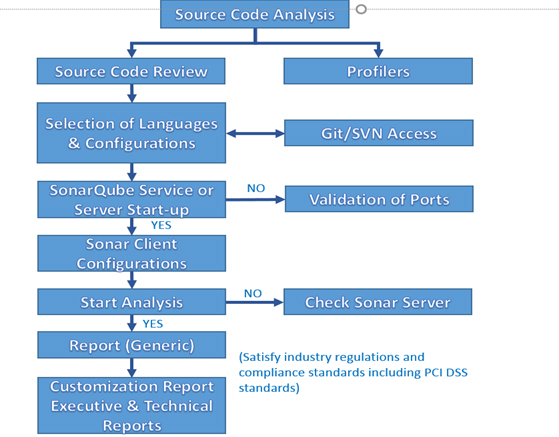
- As part of Source Code review focus on discovering hidden vulnerabilities, design flaws, and verifies if key security controls are implemented.
- SmartQE uses a combination of scanning tools to detect insecure coding practices, backdoors, injection flaws, cross site scripting flaws, insecure handling of external resources, weak cryptography
- Report Engine – Executive & Technical Reports
Vulnerability and Pen Testing
-
- Detect different kinds of well-known vulnerabilities for Mobile and Network
- Vulnerabilities Scanning/Detection with Integration of Multiple Tools
- Validation for compliance violations
- Categorization of weaknesses based on risk level
- Solution for discovered vulnerabilities & Details of security holes discovered
Compliance are configured
- HIPAA: Health Insurance Portability and Accountability Act
- NIST: National Institute of Standards and Technology
- OSSTMM: Open Source Security Testing Methodology Manual
- OWASP: Open Web Application Security Project
- PCIDSS: Payment Card Industry Data Security Standard
- SANS: SysAdmin, Audit, Network and Security
- WASC: Web Application Security Consortium
Risk Metrics Model
|
Test Name |
Risk |
|
Authentication |
|
|
Verify all pages and resources that require authentication except those specifically intended to be public. |
H |
|
Verify enforcement of all authentication controls on the server side. |
M |
|
Session Management |
|
|
Verify that the framework’s default session management control implementation is used by the application. |
H |
|
Verify that sessions are invalidated when the user logs out. |
L |
|
Access Control |
|
|
Verify that the users only access secured functions or services for which they possess specific authorization. |
H |
|
Verify that users can only access secured URLs for which they possess specific authorization. |
H |
|
Input Validation |
|
|
Verify that the runtime environment is not susceptible to buffer overflows, or that security controls prevent buffer overflows. |
H |
|
Verify that all input validation failures result in input rejection. |
M |
|
Cryptography at Rest Verification Requirement |
|
|
Verify that all cryptographic functions used to protect secrets from the application user are implemented on the server side. |
H |
|
Verify that all cryptographic modules fail securely. |
H |
|
Error Handling and Logging Verification Requirement |
|
|
Verify that the application does not send error messages or stack traces containing sensitive data that could assist an attacker, including session id. |
M |
|
Verify that all error handling is performed on trusted devices. |
M |
|
Data Protection Verification Requirement |
|
|
Verify that all forms containing sensitive information have disabled client-side caching, including auto complete features. |
H |
|
Verify that the list of sensitive data processed by this application is identified, and that there is an explicit policy on how to access this data. |
H |
Risk Scoring
|
S. No |
Vulnerability |
Severity |
Score |
|
1 |
Sensitive information Discloser |
High |
10 |
|
2 |
SQL Injection |
High |
9.7 |
|
3 |
Cross Site Request Forgery |
High |
8 |
|
4 |
Insufficient Transport Layer Security |
High |
8 |
|
5 |
Persistent Password reset link |
High |
7.6 |
|
6 |
Clickjacking |
Medium |
4.1 |
|
7 |
Server information Discloser |
Low |
2.1 |
|
8 |
Unsafe HTTP methods |
Low |
2.1 |
|
9 |
Privilege escalation Attack |
Low |
0.395 |
|
10 |
ARP spoofing, Bluetooth attacks |
Low |
0.646 |
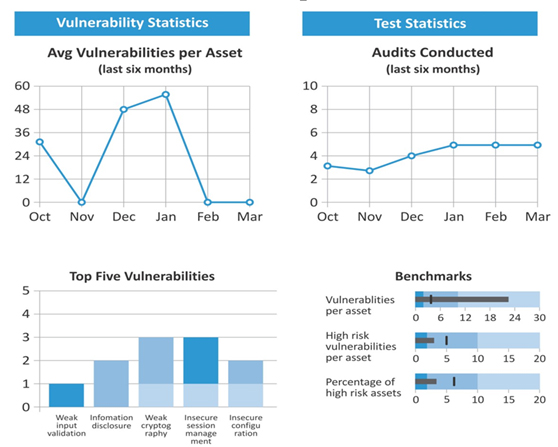
Dashboard
SmartQE’s Security Testing Dashboard consists of a comprehensive report outlining the vulnerabilities discovered during the cycle along with additional information such as screenshots and reproduction steps to facilitate ease of understanding. The vulnerabilities detected are scored with respect to industry standards
Customizable Test reports are generated automatically after each test execution along with the recommendations. Customers can figure out overall security posture based on the test results. This section also lists count of vulnerabilities by their score and severity.
|
ST Tools/Technologies |
|
|
Mobile Application Security Tools |
Drozer, Dex2jar, Quart |
|
Source Code Analysis |
Sonar Qube, Pyflakes and flake8 |
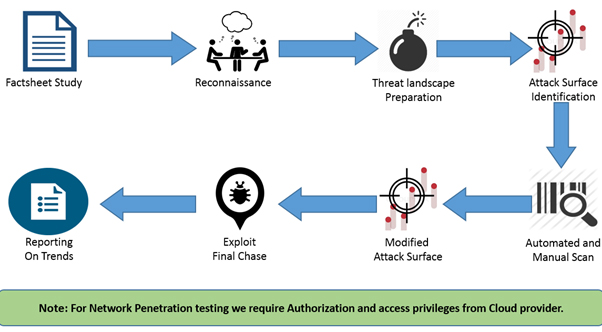
Methodology
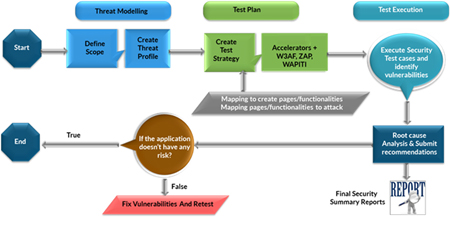
Stage 1 – Information Gathering
This stage provides the team with information about the target(s) at hand. It includes the gathering of both technical details on the target application, as well as gathering publicly available information.
- Gather the information from the client regarding the specifications of the Mobile app under test.
- Understand the client requirements on the components of the Mobile App (iOS and Android support OS, N/W and device etc..)
- Come to an agreement with the client for the application vulnerability assessment to be performed prior to deployment either on real time or on test bed
Stage 2 – Planning and Analysis
This stage represents the collation of the information gathered in Stage 1. Once this information is organized, a series of actions are planned. This stage includes attack planning and the overall approach for the audit in question, as well as formalizing which targets require further research in Stage 3.
- Define the scope based on the nature, timing and extent of the evaluation.
- Verify that no test will bring down any associated application/product prior to the product/application going live.
- Investigate and use available automated tools to perform web application vulnerability assessments and then plan for testing the application prior to deployment in the live environment.
Stage 3 – Vulnerability Detection
An exercise to assess the robustness of the infrastructure on which the Mobile app is hosted and includes identification of vulnerability types found by Mobile app vulnerability assessment and create a security test framework depending on the client environment.
Stage 4 – Penetration Testing
- Perform the attacks on the submitted App’s either locally or remotely.
- Assess possible methods of attacks based on identification of vulnerabilities during the vulnerability assessment.
- Execute exploits on the client Mobile environment.
- Verify results with the earlier vulnerability assessments.
Stage 5 – Reporting
A comprehensive report detailing the findings along with supporting snapshots and video files are furnished. A detailed analysis is conducted on the identified vulnerabilities found and attempt is made to eliminate all false positive vulnerabilities and make a detailed step by step recommendations in order to enable to fortify their Mobile Web and app.
- Executive Report: BA & Top Management – It is graphical Visualisation of number of vulnerabilities identified by different tools
- Vulnerability Summary – High, Medium & Small
- Technical Reports – Detailed Report
- Details of Vulnerability
- Content Security Policy
- In Which URL this is missing /Instance
- Solution to avoid this kind of vulnerability along with references
- CWE Id & WASC Id – we can search from exploit DB regarding the references
- We can also generate Tool Wise Report
Validation types
Reconnaissance Attack
In this kind of attack, an adversary collects as much information about your network as needed for other attacks. This information includes IP address range, server location, running OS, software version, types of devices etc. Packet capturing software, Ping command, traceroute command, whois lookup are some example tools which can be used to collect this information. Adversary will use this information in mapping your infrastructure for next possible attack.
Passive Attacks
In this attack an adversary deploys a sniffer tool and waits for sensitive information to be captured. This information can be used for other types of attacks. It includes packet sniffer tools, traffic analysis software, filtering clear text passwords from unencrypted traffic and seeking authentication information from unprotected communication. Once an adversary found any sensitive or authentication information, he will use that without the knowledge of the user.
Active Attack
In this attack an adversary does not wait for any sensitive or authentication information. He actively tries to break or bypass the secured systems. It includes viruses, worms, trojan horses, stealing login information, inserting malicious code and penetrating network backbone. Active attacks are the most dangerous in natures. It results in disclosing sensitive information, modification of data or complete data lost.
Distributed Attack
In this attack an adversary hides malicious code in trusted software. Later this software is distributed to many other users through the internet without their knowledge. Once end user installs infected software, it starts sending sensitive information to the adversary silently. Pirated software is heavily used for this purpose.
Insider Attack
According to a survey more than 70% attacks are insider. Insider attacks are divided in two categories; intentionally and accidentally. In intentionally attack, an attacker intentionally damage network infrastructure or data. Usually intentionally attacks are done by disgruntled or frustrated employees for money or revenge. In accidentally attack, damages are done by the carelessness or lack of knowledge.
Phishing Attack
Phishing attack is gaining popularity from last couple of years. In this attack an adversary creates fake email address or website which looks like a reputed mail address or popular site. Later attacker sends email using their name. These emails contain convincing message, some time with a link that leads to a fake site. This fake site looks exactly same as original site. Without knowing the truth user tries to log on with their account information, hacker records this authentication information and uses it on real site.
Hijack attack
This attack usually takes place between running sessions. Hacker joins a running session and silent disconnects other party. Then he starts communicating with active parties by using the identity of disconnected party. Active party thinks that he is talking with original party and may send sensitive information to the adversary.
Spoof attack
In this kind of attack an adversary changes the sources address of packet so receiver assumes that packet comes from someone else. This technique is typically used to bypass the firewall rules.
Buffer overflow attack
This attack is part of DoS technique. In this attack an adversary sends more data to an application than its buffer size. It results in failure of service. This attack is usually used to halt a service or server.
Exploit attack
Exploit attack is used after Reconnaissance attack. Once an attacker learned from reconnaissance attack that which OS or software is running on target system, he starts exploiting vulnerability in that particular software or OS.
Password attack
In this attack an adversary tries to login with guessed password. Two popular methods for this attack are dictionary attack and brute force attack. In brute force method, an adversary tires with all possible combinations. In dictionary method, an adversary tires with a word list of potential passwords.
Packet capturing attack
This attack is part of passive attack. In this attack an attacker uses a packet capturing software which captures all packets from wire. Later he extracts information from these packets. This information can be used to deploy several kinds of other attacks.
Ping sweep attack
In this attack an attacker pings all possible IP addresses on a subnet to find out which hosts are up. Once he finds an up system, he tries to scan the listening ports. From listing ports, he can learn about the type of services running on that system. Once he figures out the services, he can try to exploit the vulnerabilities associated with those services.
DNS Query attack
DNS queries are used to discover information about public server on the internet. All OS includes the tool for DNS queries such as nslookup in Windows, Dig and Host in Linux. These tools query a DNS server for information about specified domain. DNS server respond with internal information such as Server IP address, Email Server, technical contacts etc. An adversary can use this information in phishing or ping attack.
MiTM attacks
In this attack an adversary captures data from middle of transmission and changes it, then send it again to the destination. Receiving person thinks that this message came from original source.
Denial of Service Attacks
DoS attack is a series of attacks. In this attack an adversary tires to misuse the legitimate services. Several networking tools are available for troubleshooting. An attacker uses these tools for evil purpose. For example, ping command is used to test the connectivity between two hosts. An adversary can use this command to continuously ping a host with oversized packets. In such a situation target host will be too busy in replying (of ping) that it will not be able run other services.
Session Riding
Session riding happens when an attacker steals a user’s cookie to use the application in the name of the user. An attacker might also use CSRF attacks in order to trick the user into sending authenticated requests to arbitrary web sites to achieve various things.
Virtual Machine Escape
In virtualized environments, the physical servers run multiple virtual machines on top of hypervisors. An attacker can exploit a hypervisor remotely by using a vulnerability present in the hypervisor itself – such vulnerabilities are quite rare, but they do exist. Additionally, a virtual machine can escape from the virtualized sandbox environment and gain access to the hypervisor and consequentially all the virtual machines running on it.
Reliability and Availability of Service
We expect our cloud services and applications to always be available when we need them, which is one of the reasons for moving to the cloud. But this isn’t always the case, especially in bad weather with a lot of lightning where power outages are common. The CSPs have uninterrupted power supplies, but even those can sometimes fail, so we can’t rely on cloud services to be up and running 100% of the time. We have to take a little downtime into consideration, but that’s the same when running our own private cloud.
Insecure Cryptography
Cryptography algorithms usually require random number generators, which use unpredictable sources of information to generate actual random numbers, which is required to obtain a large entropy pool. If the random number generators are providing only a small entropy pool, the numbers can be brute forced. In client computers, the primary source of randomization is user mouse movement and key presses, but servers are mostly running without user interaction, which consequentially means lower number of randomization sources. Therefore, the virtual machines must rely on the sources they have available, which could result in easily guessable numbers that don’t provide much entropy in cryptographic algorithms.
Data Protection and Portability
When choosing to switch the cloud service provider for a cheaper one, we have to address the problem of data movement and deletion.
Secure Data Transmission
When transferring the data from clients to the cloud, the data needs to be transferred by using an encrypted secure communication channel like SSL/TLS. This prevents different attacks like MITM attacks, where the data could be stolen by an attacker intercepting our communication.
Insecure APIs
Various cloud services on the Internet are exposed by application programming interfaces. Since the APIs are accessible from anywhere on the Internet, malicious attackers can use them to compromise the confidentiality and integrity of the enterprise customers. An attacker gaining a token used by a customer to access the service through service API can use the same token to manipulate the customer’s data. Therefore, it’s imperative that cloud services provide a secure API, rendering such attacks worthless.
Malicious Insiders
Employees working at cloud service provider could have complete access to the company resources. Therefore, cloud service providers must have proper security measures in place to track employee actions like viewing a customer’s data. Since cloud service provides often don’t follow the best security guidelines and don’t implement a security policy, employees can gather confidential information from arbitrary customers without being detected.
Shared Technology Issues
The cloud service SaaS/PasS/IaaS providers use scalable infrastructure to support multiple tenants which share the underlying infrastructure. Directly on the hardware layer, there are hypervisors running multiple virtual machines, themselves running multiple applications.
Data Loss
The data stored in the cloud could be lost due to the hard drive failure.
Data Breach
When a virtual machine is able to access the data from another virtual machine on the same physical host, a data breach occurs – the problem is much more prevalent when the tenants of the two virtual machines are different customers. The side-channel attacks are valid attack vectors and need to be addressed in everyday situations. A side-channel attack occurs when a virtual machine can use a shared component like processor’s cache to access the data of another virtual machine running on the same physical host.
Account/Service Hijacking
It’s often the case that only a password is required to access our account in the cloud and manipulate the data, which is why the usage of two-factor authentication is preferred. Nevertheless, an attacker gaining access to our account can manipulate and change the data and therefore make the data untrustworthy. An attacker having access to the cloud virtual machine hosting our business website can include a malicious code into the web page to attack users visiting our web page – this is known as the watering hole attack. An attacker can also disrupt the service by turning off the web server serving our website, rendering it inaccessible.
Unknown Risk Profile
We have to take all security implications into account when moving to the cloud, including constant software security updates, monitoring networks with IDS/IPS systems, log monitoring, integrating SIEM into the network, etc. There might be multiple attacks that haven’t even been discovered yet, but they might prove to be highly threatening in the years to come.
Denial of Service
An attacker can issue a denial of service attack against the cloud service to render it inaccessible, therefore disrupting the service. There are a number of ways an attacker can disrupt the service in a virtualized cloud environment: by using all its CPU, RAM, disk space or network bandwidth.
Benefits Offering by SmartQE:
- Heuristic Evaluation
- Reduce Security testing cost by half
- Validation of Controls & Vulnerability Coverage
- No memory, file and N/W attacks at runtime
- No business interruption and 95% risk free enterprise security surface protection platform from attacks and malwares
- Helped meet Regulatory Compliances (NIST, PCIDSS, SANS and WASC) through detailed reporting & documentation of Test Results
- Minimized Attacks/ Application Vulnerabilities
- Increase Business Continuity & Zero Business disruption
- Remediation recommendations against identified vulnerabilities
- Continuous security testing recommendations to achieve security assurance
- Ensuring in time & appropriate security testing helped identify high-severity security defects, & prevented potential loss of critical end customer data and secured their transactions
- Increase Business Continuity and availability
- Manage Security Risk Properly
- Protect Clients and Partners Data, Comply with Regulation or Security Certification
- Compliance with Industry Standards, Avoid Network Downtime
- Identifying higher-risk vulnerabilities, that may be difficult or impossible to detect with automated network or application vulnerability scanning software
- Assessing the magnitude of potential business and operational impacts of successful attacks
- Testing the ability of network defenders to successfully detect and respond to the attacks
