Web and API Security testing with SmartQE
SmartQE is a containerized Cloud based SaaS security opensource framework for Web and API code inspections and to validate against standards. SmartQE can easily integrate with CI/CD platform and tools. It is a single security framework integration of tools to perform assessment, vulnerability, penetration, code, infrastructure, network and integrations security validation against compliances and standards. SmartQE is integrated with ZAP, iHScanner, Wapiti, W3af, SQLMap and NMAP opensource security tools.
SmartQE supports Web, API, Mobile, Cloud, data, information and Network security. A deep dive security assessment reporting and recommendations help an organization to prevent potential cyber threats.
SmartQE security testing leverages the latest technologies to assess vulnerabilities, reduce threat and maximize security effectiveness. These include hundreds of tests per week, static and dynamic software analysis, cooperative and uncooperative engagements, network emulation with endpoints and processes for turning threat indicators into defensive actions.
Challenges:
- Payment and Banking Hacks - Every online communication is potentially vulnerable, including mobile and online payments. Numerous attacks against financial institutions are reported daily
- Next-Generation Heartbleed - Open-source weaknesses like Shellshock, Poodle and Heartbleed challenged the resolve of many institutions last year
- Advanced Phishing Scams - Most phishing scams are fairly transparent, and sophisticated users rarely fall for pop-ups asking for a password even though less-sophisticated users are still vulnerable to these
- Cyber Insurance is the New Cybersecurity Posture
- Card-Not-Present (CNP) fraud will be growing - digital wallet solutions, point-of-sale system fraud and counterfeit credit cards
- Increased Security Threats across the globe
- Organization electronic network and data needs to be protected against unauthorized attacks.
- Adoption of Cloud & Mobile applications
- Integration of Third-party API’s, services and micro services
Security Testing Service Offerings/Solutions:
- Discovery - The purpose of this stage is to identify systems within scope and the services in use. Understand organizations security posture.
- Vulnerability Assessment - We conduct assessments in the areas of network security vulnerabilities, end point security vulnerabilities, cloud and mobile vulnerabilities, threat analysis, vulnerability risk assessment. These assessments help customers to understand the vulnerabilities in their land scape and help them to plan their mitigations.
- Vulnerability Testing - We perform vulnerability Testing as part of the vulnerability assessment to determine security holes and gaps in the systems.
- Penetration Testing - After determining the vulnerabilities that exists in the systems, mobile, Cloud, infrastructure, servers & networks, we perform penetration testing to check if security issues exist
- Security Compliance Testing and Audit - To Identify, resolve and reduce attacks and maintain Security Compliance. We perform application and network security assessment, information security risk assessment and security threat assessment
- Security Code and Architecture Review - Verification that industry or internal security standards have been applied to system components or product. This is typically completed through gap analysis and utilises build / code reviews or by reviewing design documents and architecture diagrams. This activity does not utilise any of the earlier approaches (Vulnerability Assessment, Security Assessment, Penetration Testing, Security Audit)
- IT Security and Consultation - Delivers a variety of reports to verify your application security posture and provide actionable intelligence to help you quickly prioritize and remediate any exposures. Provides details about the application infrastructure such as operating systems, framework used, back end database etc. with appropriate recommendations
Expert guidance in orchestrating the security need to stop insider threats and data breaches. We will help you:
- Define business requirements and scope
- Collect relevant data to be used in policy design and testing
- Identify steps for optimal implementation, evaluation and tuning of your security solution.
- Network Penetration testing - Identify vulnerabilities and risks in the network
- External Penetration Testing: External or public facing network to identify vulnerabilities that are visible to outsiders. It is done from any remote location over the internet without any explicit access permissions to the organization’s network.
- Internal Penetration Testing: Internal network to identify vulnerabilities that are visible to potential insiders, contractors, partners with malicious intent. It is done at the vicinity of organization’s network with access permissions given to the attacker to show what risk is posed to information systems by organization’s employees, contractors and guests.
Security Testing checklist:
Test execution strategy would comprise three types of tests for a web site namely:
- General Application tests
- Business logic tests
- Technology Tests
All applicable tests would be executed against the application and detailed results with sufficient evidences would be provided
|
Web Application General Checks |
|
|
S. No |
Tests |
|
1 |
Application Flooding |
|
2 |
Parameter Analysis |
|
3 |
Authorization Parameter Manipulation |
|
4 |
Application Workflow |
|
|
Authentication |
|
5 |
Check whether application is SSL enabled |
|
6 |
Authentication bypass Tests |
|
7 |
Check for default accounts |
|
8 |
Password Quality |
|
9 |
Password Reset |
|
10 |
Password Lockout |
|
11 |
Password Structure |
|
12 |
Fail Open Authentication |
|
|
Session Management |
|
13 |
Session Token Length |
|
14 |
Session Timeout |
|
15 |
Session Reuse |
|
16 |
Session Deletion |
|
17 |
Session Token Format |
|
|
Configuration Management |
|
18 |
Environment related vulnerabilities |
|
19 |
Missing patches |
|
20 |
Back-up Files and references |
|
21 |
Web Server Configuration |
|
22 |
Web Server Components |
|
23 |
Common Paths |
|
24 |
Application Admin Interfaces |
|
|
Error Handling |
|
25 |
Application Error Messages |
|
26 |
User Error Messages |
|
27 |
Data in HTML |
|
28 |
Data Protection – SSL |
|
29 |
Digital Certificate Validity and algorithms |
|
|
Input Validation |
|
30 |
Script Injection |
|
31 |
SQL Injection |
|
32 |
OS Command Injection |
|
33 |
LDAP Injection |
|
34 |
XSS Cross Site Scripting |
|
35 |
Injection flaws |
|
36 |
Cross Site Request Forgery |
|
37 |
Debug mode |
|
38 |
Thread Safety |
|
39 |
Hidden Form Field Manipulation |
|
40 |
Cookie Security |
|
41 |
Dangers of HTML Comments |
|
42 |
Malicious File inclusion |
|
43 |
Insecure Direct Object Reference |
|
44 |
Failure to restrict URL access |
|
45 |
Insecure cryptographic usage |
|
46 |
Insecure communications |
|
47 |
Command Injection |
|
48 |
HTTP Response Splitting |
|
Business Logic tests |
|
|
S. No |
Tests |
|
1 |
Identify logical threats |
|
2 |
Understand the functionality |
|
3 |
Perform logical tests |
|
4 |
Check work flow patterns |
|
5 |
Verify user privilege and bypass flaws |
|
6 |
Verify flaws in user access rights |
|
7 |
Boundary value tests |
|
Tests by Technology |
||
|
S. No |
Tests |
|
|
1 |
Input Validation |
|
|
2 |
Injection Attacks |
|
|
3 |
Authentication |
|
|
4 |
Session Management |
|
|
5 |
Authorization |
|
|
6 |
Encryption |
|
|
7 |
Error Handling & Logging |
|
|
8 |
Web Services Security |
|
|
9 |
Patch Levels |
|
|
10 |
Information Disclosure |
|
|
11 |
Cookie Poisoning |
|
|
12 |
SQL Injection |
|
|
13 |
Cross Site Scripting |
|
|
14 |
AJAX Tests |
|
|
15 |
Resource Tampering |
|
|
16 |
Unreleased Resources |
|
|
17 |
Cookie Security |
|
List of features are integrated with SmartQE
|
Features |
Wapiti |
W3af |
ZAP |
Wfuzz |
SQLMap |
|
GUI |
No |
Yes |
Yes |
No |
Yes |
|
SQL injection |
Yes |
Yes |
Yes |
Yes |
Yes |
|
Authentication support |
Yes |
Yes |
Yes |
Yes |
No |
|
Automatic scanning |
No |
No |
Yes |
No |
No |
|
XSS(Cross-site scripting) injection |
Yes |
Yes |
Yes |
No |
No |
|
Cookie not HttpOnly flag |
No |
No |
Yes |
No |
No |
|
Missing anti-CSRF tokens and security headers |
No |
No |
Yes |
No |
No |
|
Private IP disclosure |
No |
No |
Yes |
No |
No |
|
Finding Buffer overflow issues |
No |
Yes |
No |
No |
No |
|
Command Execution detection |
Yes |
No |
No |
Yes |
No |
|
File disclosure |
Yes |
No |
No |
No |
No |
|
Shellshock or Bash bug |
Yes |
No |
No |
No |
No |
|
SSRF (Server-Side Request Forgery) |
Yes |
No |
No |
No |
No |
|
XXE (XML External Entity) Injection |
Yes |
No |
No |
No |
No |
|
Wapiti |
W3af |
ZAP |
Wfuzz |
SQLMap |
|
Allows authentication via different methods, including Kerberos and NTLM |
Authentication support |
Automatic scanning |
Authentication support |
Automates the process of finding SQL injection vulnerabilities |
|
Operates like a fuzzer |
Offers intuitive GUI interface |
Easy to use |
Cookies fuzzing |
Can also be used for security testing a website |
|
Supports both GET and POST HTTP methods for attacks |
Output can be logged into a console, a file or email |
Multi-platform, Rest-based API. Support for authentication. Uses traditional and powerful AJAX spiders |
Multi-threading |
Robust detection engine, Supports a range of databases, including MySQL, Oracle, and PostgreSQL |
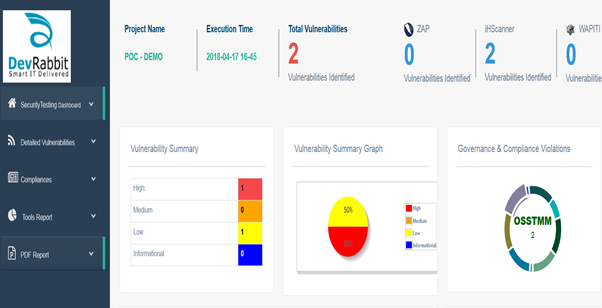
Web App Security Testing Dashboard
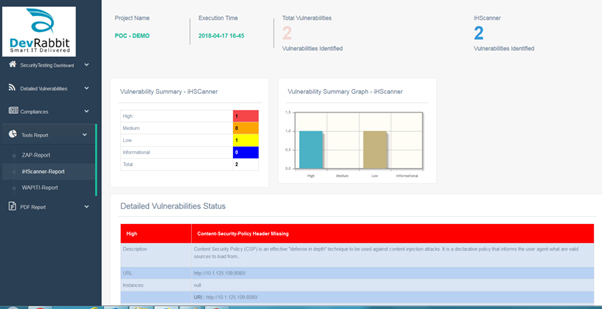
iHScanner Report
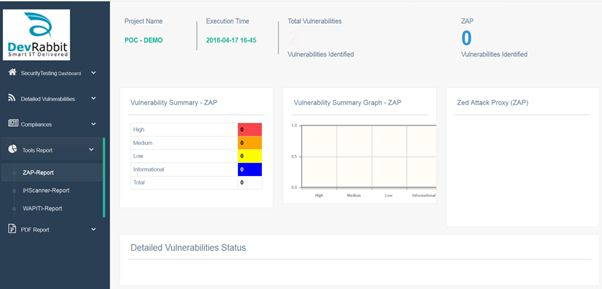
ZAP Report
Compliances are integrated to SmartQE
- HIPAA - Health Insurance Portability and Accountability Act
- NIST - National Institute of Standards and Technology
- OSSTMM - Open Source Security Testing Methodology Manual
- OWASP - Open Web Application Security Project
- PCIDSS - Payment Card Industry Data Security Standard
- SANS – Sys Admin, Audit, Network and Security
- WASC - Web Application Security Consortium
Business Benefits
- Heuristic Evaluation
- Validation of Controls & Vulnerability Coverage
- No memory, file and N/W attacks at runtime
- No business interruption and 95% risk free enterprise security surface protection platform from attacks and malwares
- Helped meet Regulatory Compliances (NIST, PCIDSS, SANS and WASC) through detailed reporting & documentation of Test Results
- Minimized Attacks/ Application Vulnerabilities
- Increase Business Continuity & Zero Business disruption
- Remediation recommendations against identified vulnerabilities
- Continuous security testing recommendations to achieve security assurance
Ensuring in time & appropriate security testing helped identify high-severity security defects, & prevented potential loss of critical end customer data and secured their transactions
SmartQE’s Key Differentiators :
SmartQE performs
- 360 degrees of Security validation against standards/Compliance, domains and technologies
- Infrastructure security standards, venerability and Pen testing
- Source Code Security Standards and venerability assessment
- Application security standards, venerability and Pen testing
- Mobile Security security standards, venerability and Pen testing
- Vulnerability assessment for Kubernetes, dockers, firewall and load balancer
- Network Penetration Testing
- Enterprise product (SAP and Oracle EBS) security standards, venerability and Pen testing
- Security standards, venerability and Pen testing with opensource tools and Python programs
- End point automation for security standards, venerability and Pen testing
- Executive summary and detailed reports help to determine security risks
- Opensource security tools, standards, technologies are integrated into one platform – SmartQE Security testing Accelerator.
